US offers $15M for details on Conti ransomware | CryptoSlate
The U.S.Office of State set two separate bounties for information on the Conti ransomware arranged criminal offense group totaling $15 million.
Any information and facts that helps detect or identify the Conti team leaders will be awarded up to $10 million. Furthermore, $5 million will be awarded for any info that leads to the arrest of men and women conspiring with the Conti team.
The rewards are made available below the Division of State’s Transnational Arranged Crime Benefits Plan (TOCRP) and can be claimed from any country.
Ransomware assaults
Ransomware is a style of malware that threatens to delete or publish non-public information and facts until a ransom is paid.
Overall price gained by ransomware attacks amongst the a long time 2016-2021 (by means of Chainalysis)
Ransomware assaults peaked in 2020 by achieving $692 million in total benefit, in accordance to Chainalysis. The whole amount paid in ransom remained in excess of $600 million as of 2021. Nevertheless, the slight decrease in confiscated complete worth doesn’t signify that the danger is also degrading.
The report states:
“Despite these numbers, anecdotal evidence, in addition the fact that ransomware income in the initial 50 percent of 2021 exceeded that of the first 50 percent of 2020, indicates to us that 2021 will at some point be discovered to have been an even even bigger year for ransomware.”
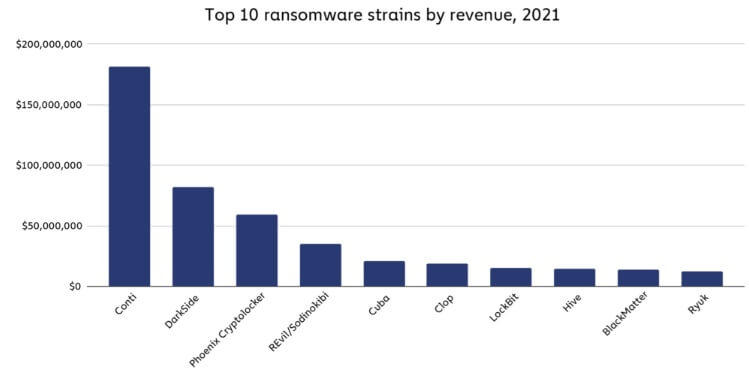
The same report breaks down the best 10 ransomware strains by revenue, exactly where Conti normally takes the to start with spot by extorting at the very least $180 million from its victims in 2021.
Conti ransomware
It is approximated that the Conti ransomware team has been energetic for in excess of two decades and has about 350 users. It was equipped to accumulate above $2.7 billion in ransom given that 2020.
In accordance to data leaked from Conti, the team uses proprietary in-home application that is much more rapidly than other most ransomware programs. All variations of Microsoft Windows are prone to their assaults.
On 21 April 2022, the group attacked the Federal government of Costa Rica and targeted at least 5 govt businesses, together with the Ministries of Finance, Science, and Technological know-how. Conti demanded a $10 million ransom and commenced leaking particular data for not getting it.
🚨 #Conti’s most recent update on the cyberattack in opposition to Costa Rica’s Ministerio de Hacienda 🇨🇷…
“If the ministry simply cannot reveal to its tax payers what is going on, we will do it 1) we have penetrated their critical infrastructure, received entry to about 800 servers, …” 👇 pic.twitter.com/wp2Y8UeGGN
— BetterCyber (@_bettercyber_) April 20, 2022
Professionals from Cyberint, who analyzed Conti debunked formerly confiscated in-group messages created in Russian and uncovered that the team adopted a properly-managed organizational composition.
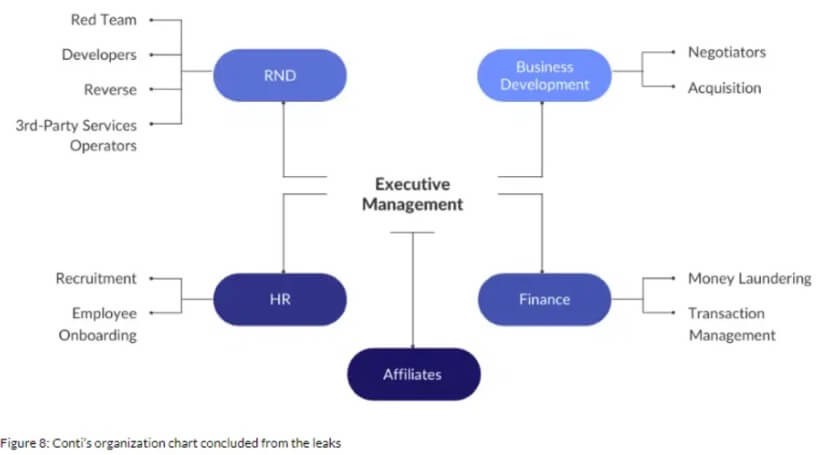
The messages also showed that the group had bodily places of work in Russia, ran overall performance critiques, and even named an “employee of the month.”
Lotem Finkelstein, the head of risk intelligence at Test Level Software program Systems, said:
“Our … assumption is that this sort of a big firm, with actual physical places of work and huge income would not be able to act in Russia without having the entire acceptance, or even some cooperation, with Russian intelligence services.”
Get an Edge on the Crypto Marketplace 👇
Turn out to be a member of CryptoSlate Edge and obtain our distinctive Discord neighborhood, a lot more exceptional content and examination.
On-chain analysis
Value snapshots
Far more context
Join now for $19/month Explore all benefits




